Deutsch | English
Protect Against Threats: Even Before They Reach You
Artifacts such as IP reputation or filenames are not useful without deeper analysis into attack methods and how that can occur in your unique context. We churn out threat intelligence, validate, and apply them to your context to provide precise steps to detect, respond, and mitigate global threats.
We continuously monitor global threats and adapt your defenses within hours of discovering an attack or collecting threat intel, so you don’t fall victim to threats that have successfully breached others.

We then analyze this data to determine which threats your organization can safely ignore—and which you need to prepare for now. We bring two actionable outcomes: tactical threat intel and strategic threat intel.
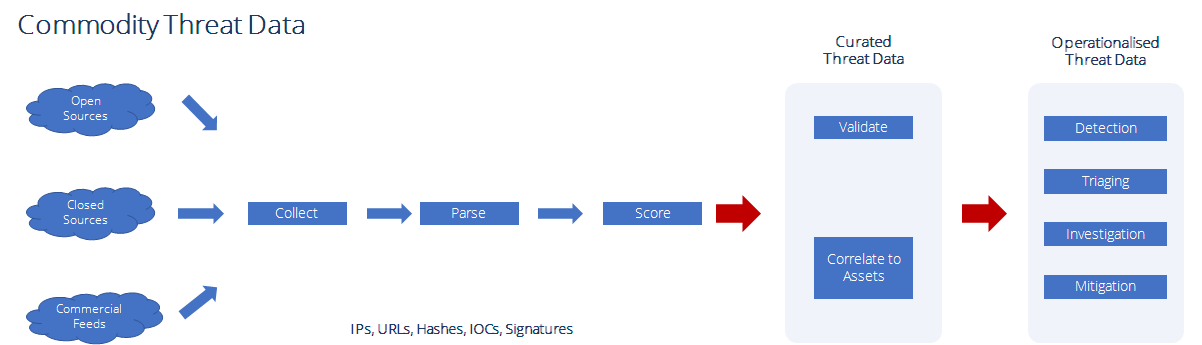
You receive our validated and curated threat intelligence in a machine-readable format. The content includes malicious IPs, URLs, files, hashes, processes, and signatures.
You can apply this data to your security products and IT devices at machine speed and quickly improve your prevention, detection, and response to threats.


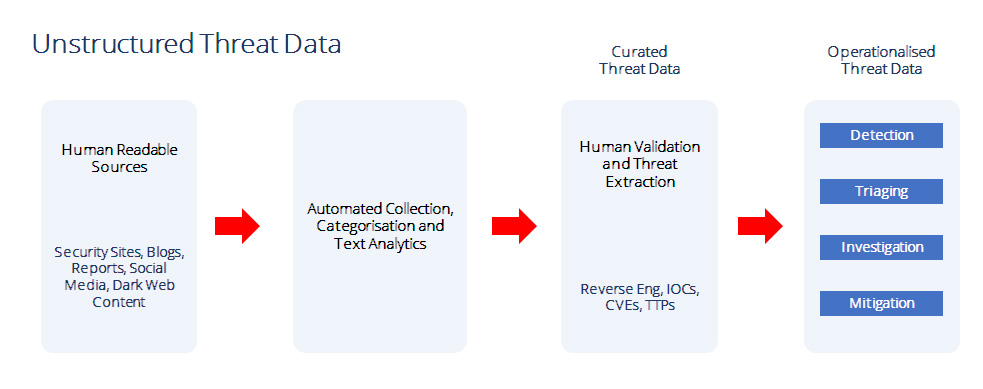
We analyze globally reported breaches and attacks, and extract key intelligence from the data. These could be malware samples, reverse engineered IOCs, specific TTPs used in the attack, the CVEs that are exploited, and other relevant data on attacks.
And based on intelligence we extract from unstructured breach data, we put together specific action items that you specifically must deploy to prevent, detect, and respond to these reported breaches.




Threat Anticipation Service is a part of our Managed Detection and Response Service (MDR). With MDR, you not only get anticipatory threat intelligence, but you also get advanced threat protection services, via: Threat Hunting, Round-the-Clock Security Monitoring, Alert Response, Incident Response, and Breach Management.
Why stop with Threat Anticipation, when you can leverage a managed service that integrates your cyber threat intelligence, and provides advanced incident detection and response?
