Deutsch | English
Look Under the Hood of a Next Generation Cyber Defense Platform
What makes the solution tick ?
Traditional SIEM-based security monitoring cannot detect complex, targeted, or unknown attacks. It is unable to analyse a high volume of varied data. In short: it is unable to defend you from next-generation cyberattacks.
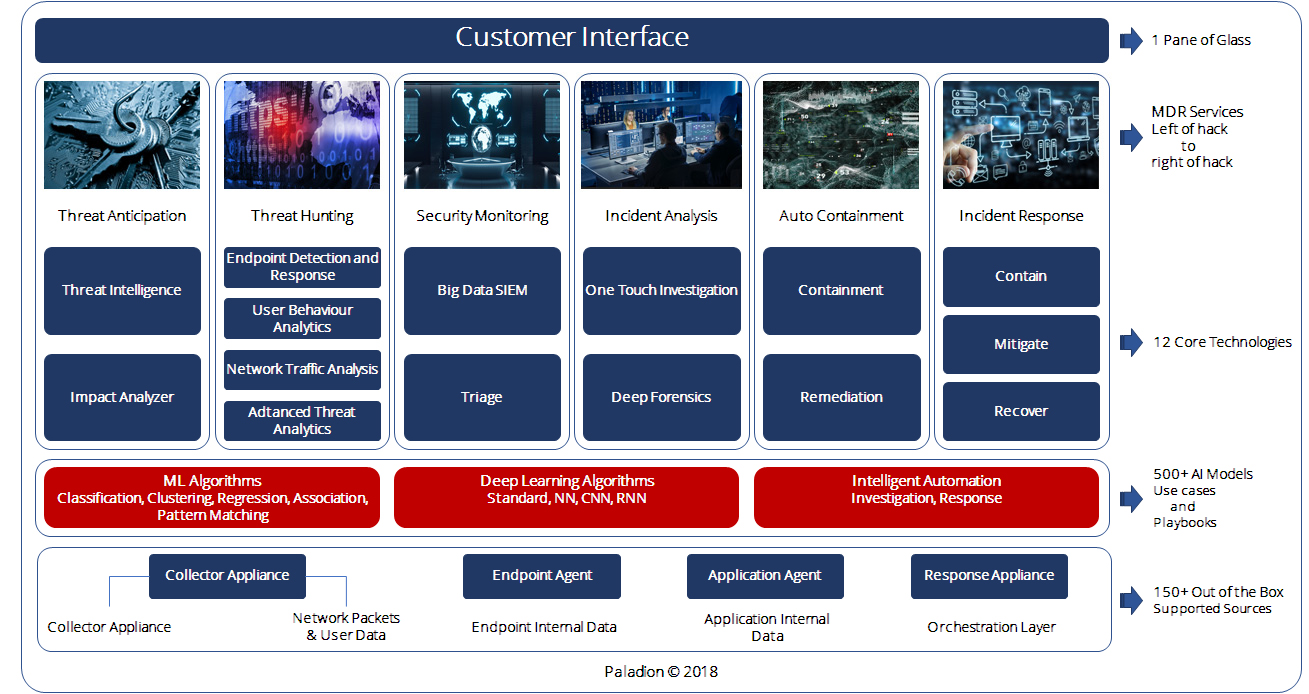
In response, we have evolved beyond SIEM, and built a truly comprehensive MDR service powered by our next-generation AI platform—AIsaac
AIsaac runs on a Hortonworks Big Data platform and uses next-generation algorithms to detect complex, targeted, and unknown attacks. With AIsaac, we can continuously analyse your organization’s data to detect your attacks in near real-time. Once a threat is detected, AIsaac accelerates and fully orchestrates your fast, accurate, and effective response to remediate your threats in minutes, not months.
Today, AIsaac offers the industry’s only fully integrated platform that enhances a full suite of “left-of-hack-to-right-of-hack” Cyber Defense services.





Responds Two days after we deployed our services for a large bank with 250,000+ endpoints, we detected a previously undetected data-theft keylogger. The malware was sending information to an external URL that had not received a blacklist score from any threat intelligence feed. However, our AI models detected anomalous beaconing behavior within terabytes of netflow traffic by utilizing information gain theory (entropy of sets) and a multivariate gaussian model. We discovered the malware had been planted five months prior, and had been sharing key logs captured from infected systems in repeated, smaller chunks at regular intervals the entire time.
Within a financial institution, we detected a drive-by-download-based infection of multiple systems. Employees of the financial institution were offered a company-sponsored course at an educational institute. They visited the educational institute’s website to acquire course details, and to register. However, the educational institute’s website had been compromised and was distributing malware, and the financial institution’s employees downloaded the malicious file using drive-by-download. Multiple systems with browser vulnerabilities at the financial institution were infected.
Our watering-hole model identified this compromised behavior through analysis of proxy traffic, netflow traffic, and EDR data. It utilized non-parametric statistical model and behavior profiling to detect the infection.
We have detected multiple data exfiltration activities, within multiple customer environments. We have successfully detected changes in data transfer behavior by comparing user’s past profiles, peer comparison analysis, and non-equal clustering techniques.
We helped to detect previously-undetected low-noise targeted attacks within multiple customer sites. Our attack association model—built on a modified version of market basket analysis—identified anomalous attack behavior from detected targeted attacker IPs. Our model’s association techniques clustered together all attacks occurring on one day. We then separated out attacks anomalous to all other attacks observed in that day, and identified the involved attacker’s IP.
We detected multiple compromised endpoints running the Trojan NsCpuCNMiner32.exe, and software that uses the infected computer’s CPU to mine the Monero digital currency. The Trojan spreads as an executable (called Photo.scr). When started, it copies itself to every drive on the infected computer, and then extracts an executable (called NsCpuCNMiner32.exe) to the %Temp% folder to launch the executable. When launched, it co-opts all available CPU processing power to mine the Monero digital currency.
We have unearthed multiple RATs planted and operationalized in our clients’ networks. These RATs attempted to create a back door within each network, and gain administrative control over the infected computer. Most RATs were unintentionally downloaded within a seemingly-innocuous user-requested program.
We leveraged our AI to determine these program’s bayesian expectancy. We then fed low-expectancy programs into our neural networks, which matched its program sequence against relevant, known malware families and classified them as bad.
We detected multiple fake programs running under the name of legitimate Windows processes. To identify these binary impersonations, we leveraged our hashcode distribution analysis technique. We uncovered programs running the command line “C:\Users\ conserve.cfsjnpt.ACMHO\ AppData\ Roaming\ svchost.exe”, running from the inappropriate directory, and thus identified as an outlier. Through reverse engineering, we revealed the executable was creating a resource fork file commonly used to hide data. We observed multiple forms of anomalous behaviour.
The age of AI-driven cyberthreats has arrived. AI-driven cybersecurity is now a necessity.
In response, many security providers are scrambling to offer their own version of AI-driven cybersecurity. Unfortunately, many are simply MSSPs, and other last-generation providers, layering an off-the-shelf AI platform to make their outdated services appear relevant.
In contrast, Paladion’s AI-driven MDR service is built on solid ground. We leverage 17+ years of experience delivering cyber defense to over 700 clients in a diverse range of industries and geographies. Our AI platform—AIsaac—delivers high-speed detection by deploying comprehensive techniques that include supervised, unsupervised, deep learning, and NLP. AIsaac augments our 1,000+ globally-located cybersecurity experts, allowing them to process billions of events.
The result: Paladion executes detection & response across the full lifecycle of a threat in minutes— not months.
To detect and stop next-generation attacks threatening your organization, contact Paladion today to schedule your free demo and consultation.