Deutsch | English
Complete a Security Control Assessment with our Configuration Audit
Performing a secure configuration review provides visibility on:
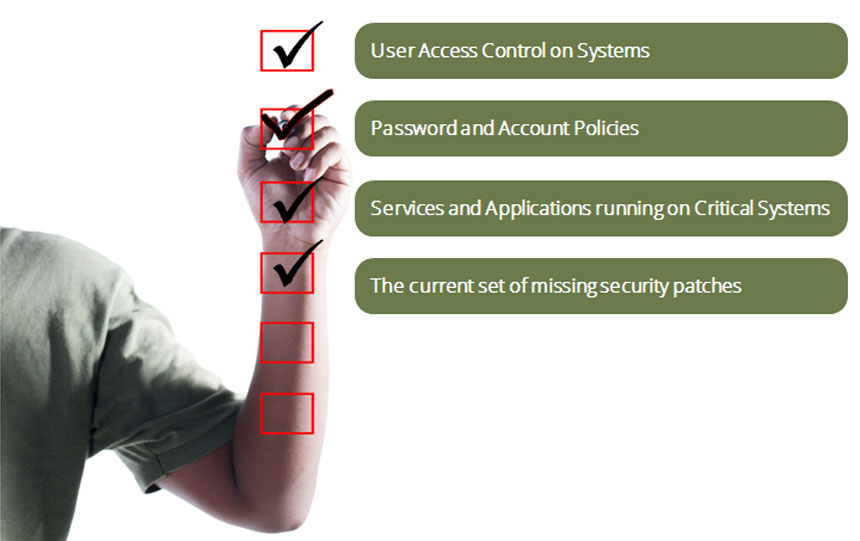
A secure configuration audit checks every facet of your network for the vulnerabilities hackers exploit to gain access. This includes operating systems, your network, and databases.
Our comprehensive audit process gives you a comprehensive view of your security posture

The audit process begins with script execution as well as a manual collection of your current configuration settings.

We then continue by conducting a comparison of the script output or the manually collected settings against established Paladion baseline settings.

After the audit is complete we provide a safe/unsafe status check with detailed descriptions of unsafe findings and discuss those findings with administrators to better understand the client’s environment.

At the conclusion of the secure configuration audit, our team of experts provides a final report with detailed findings, a risk rating, and suggestions for mitigating risk.

We have support for close to 50 common platforms that include operating systems, web servers, network devices, and firewalls. In addition, our databases and configuration audit checklists and policies comply with CIS and NIST standards.